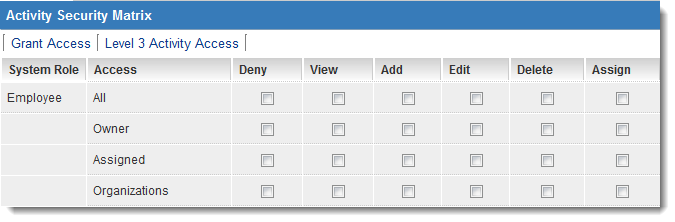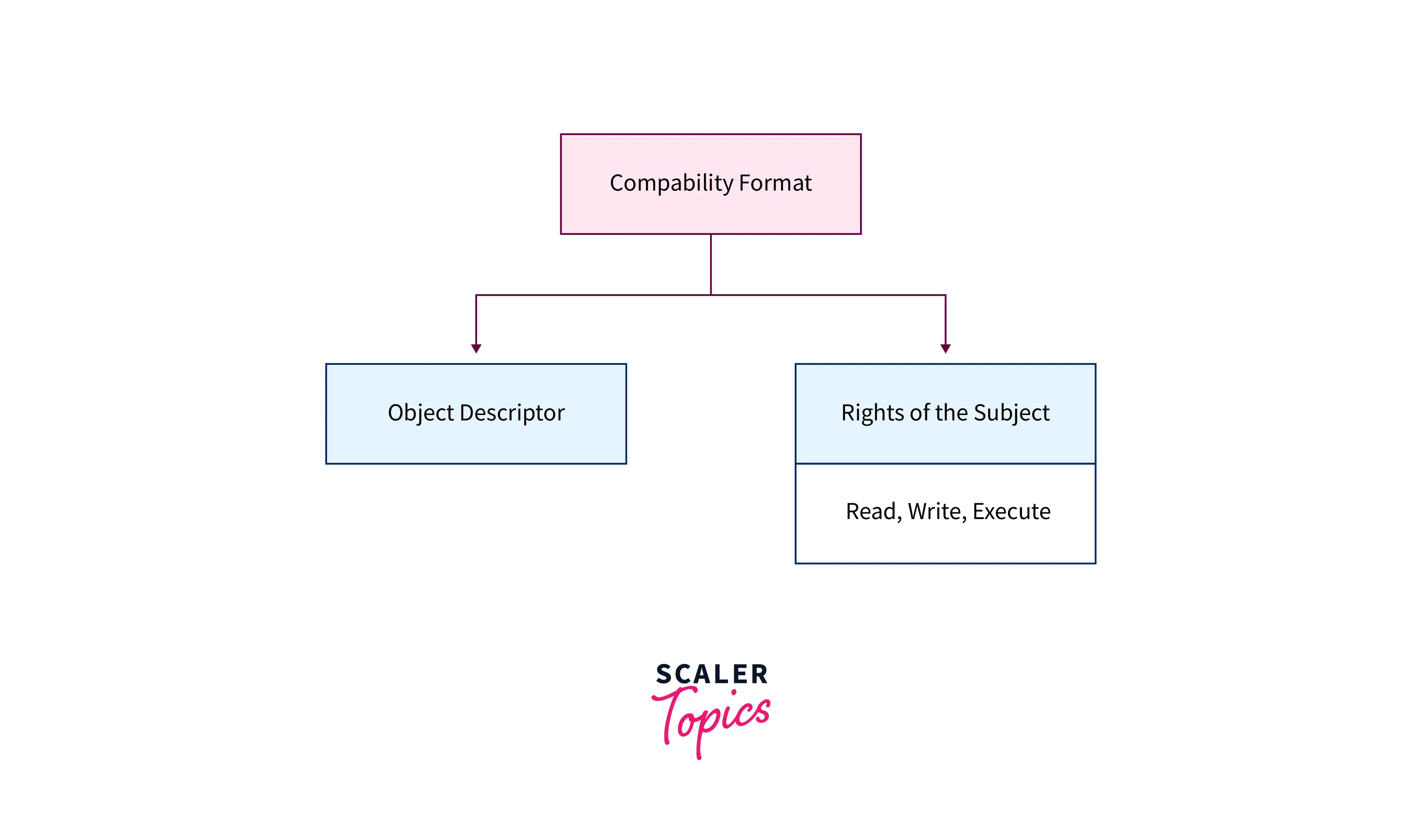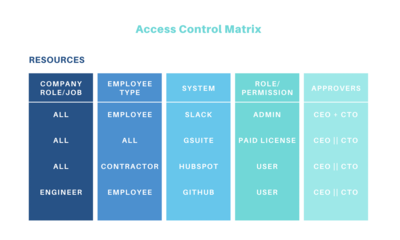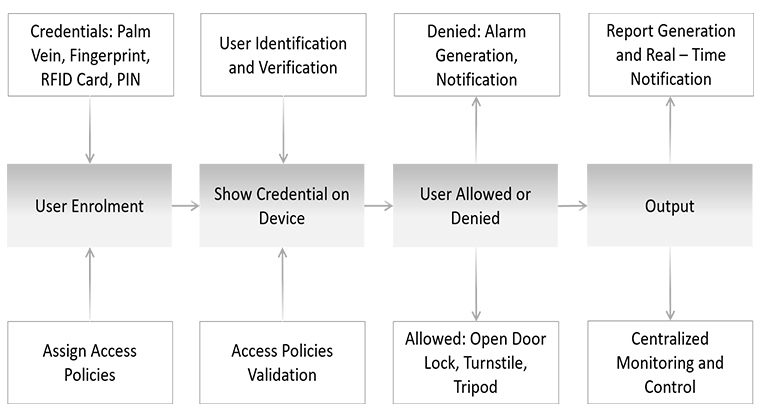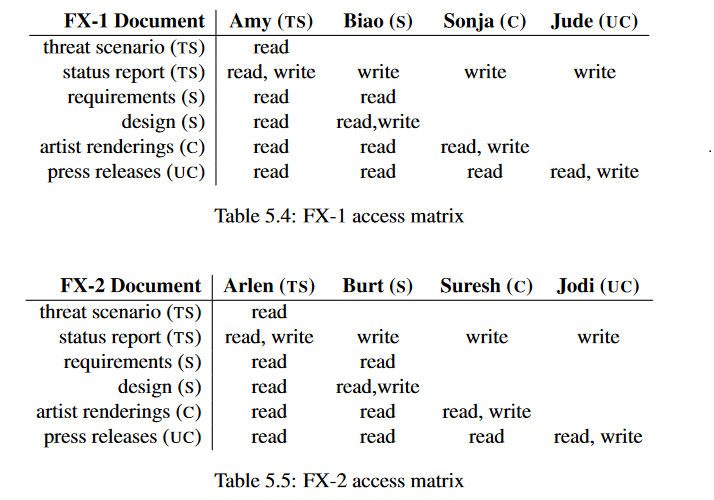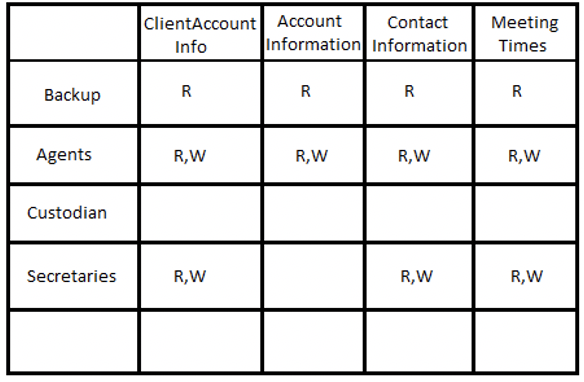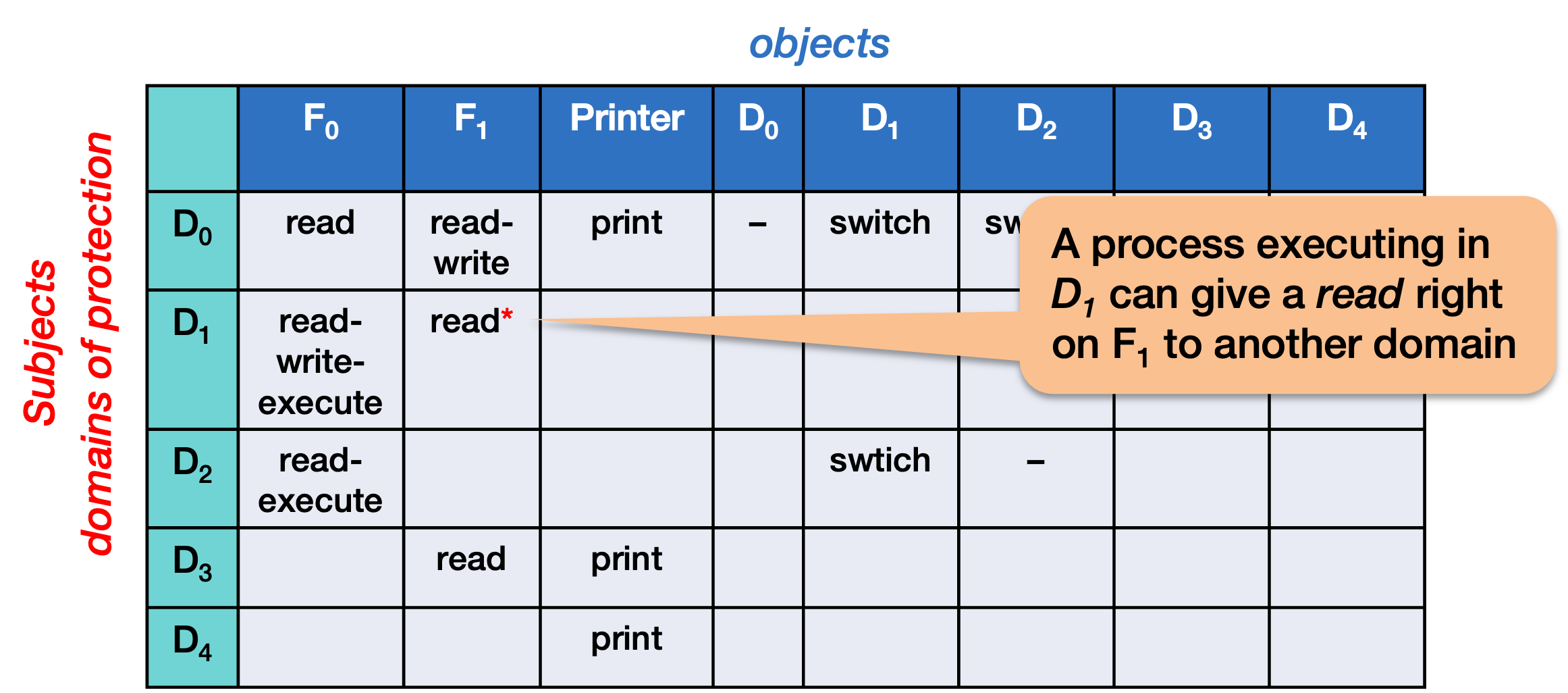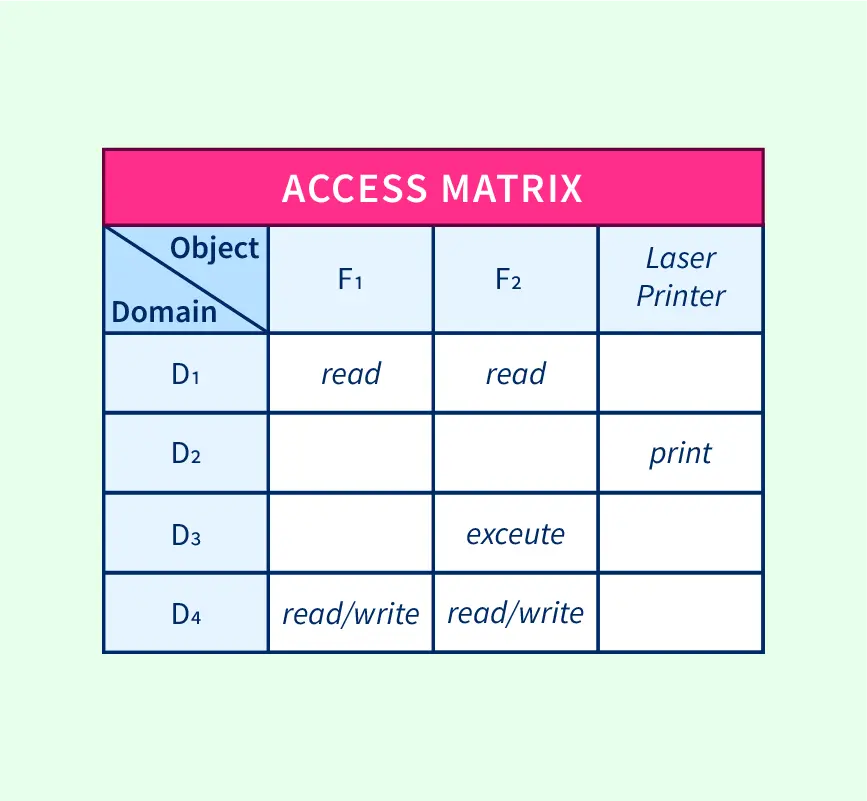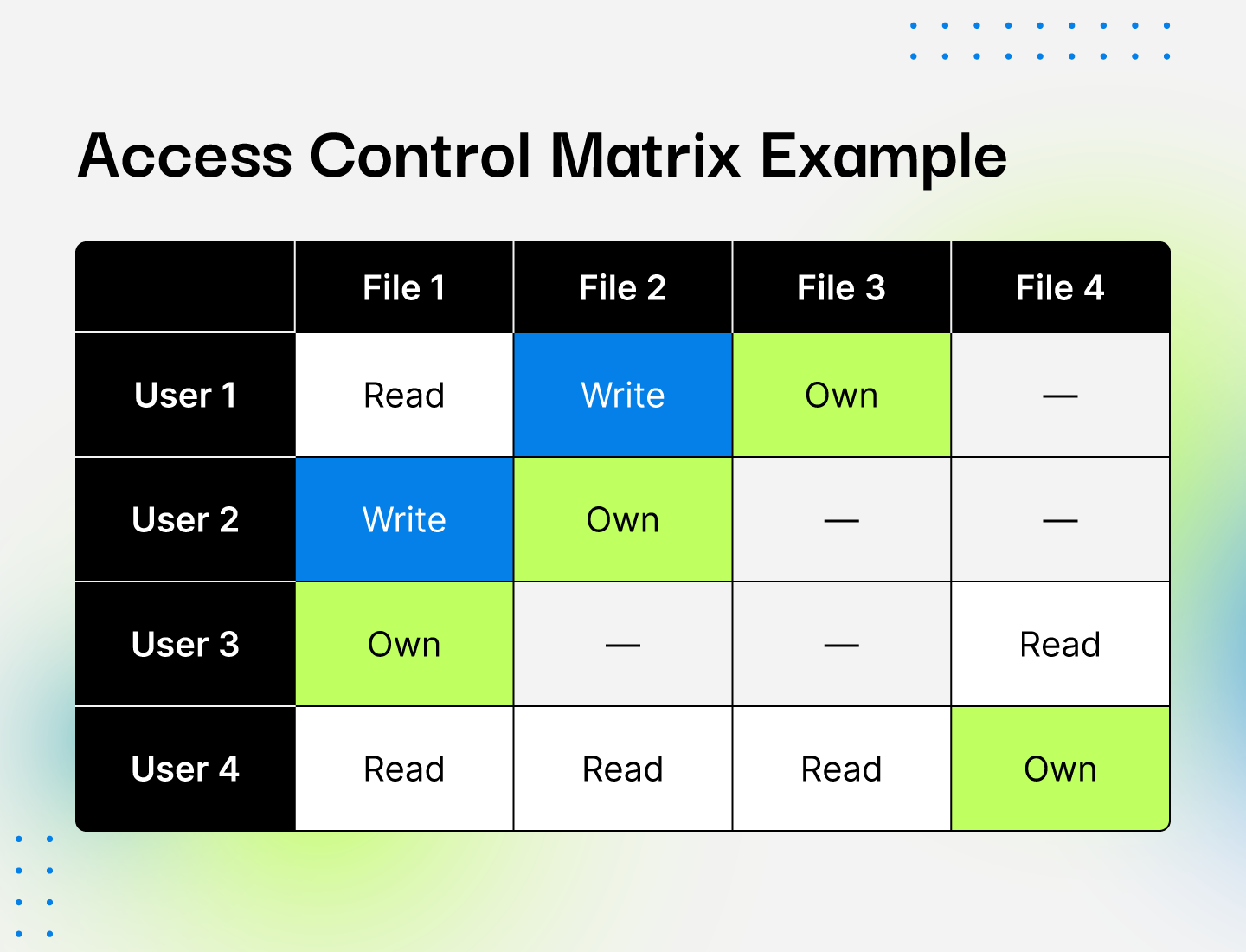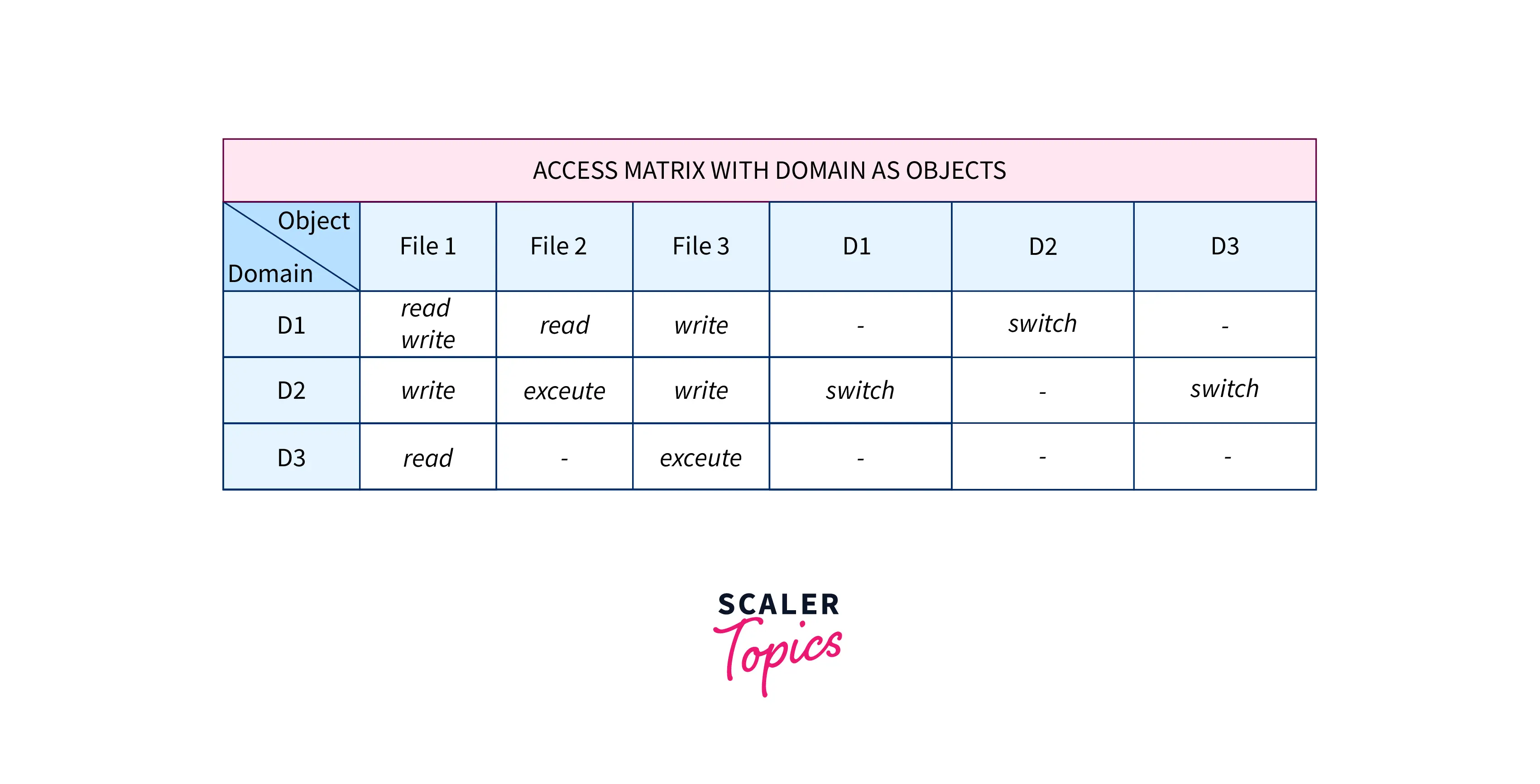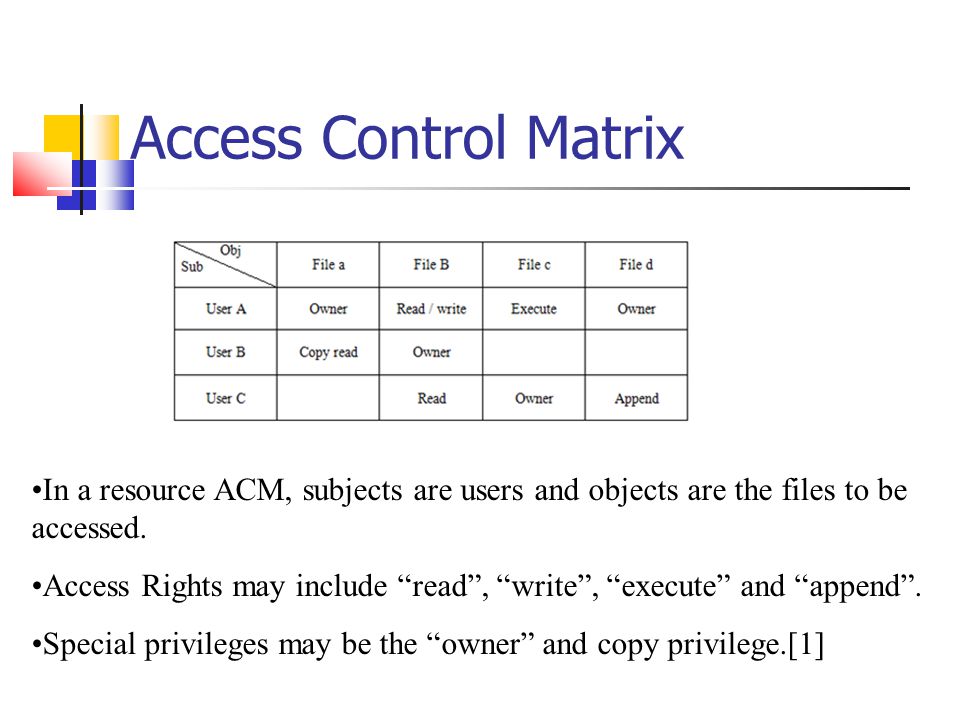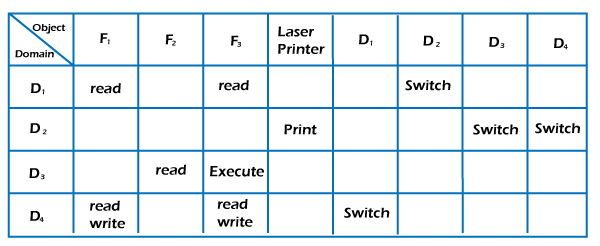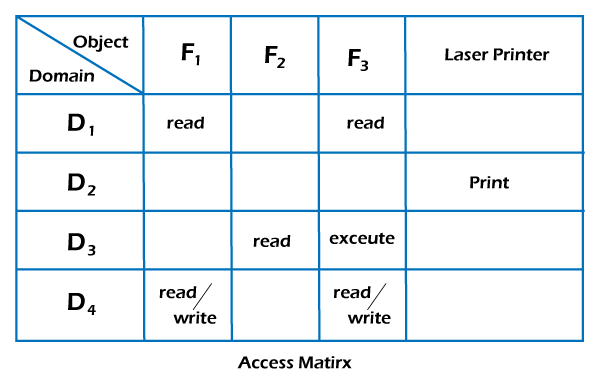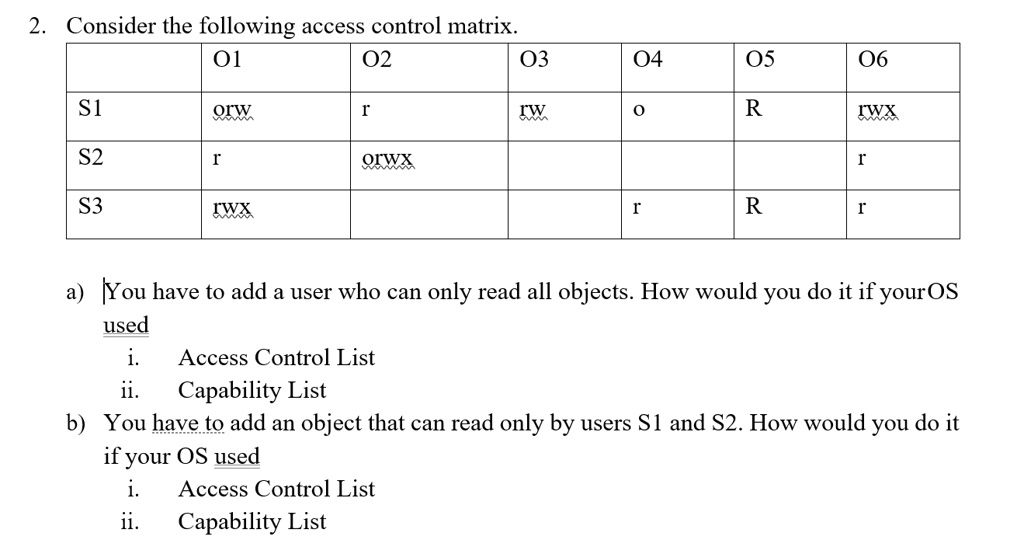
SOLVED: Consider the following access control matrix: | | 01 | 02 | 03 | 04 | 05 | 06 | |—|—–|——|——|——|——|——| | s1| orw | r | rw | 0

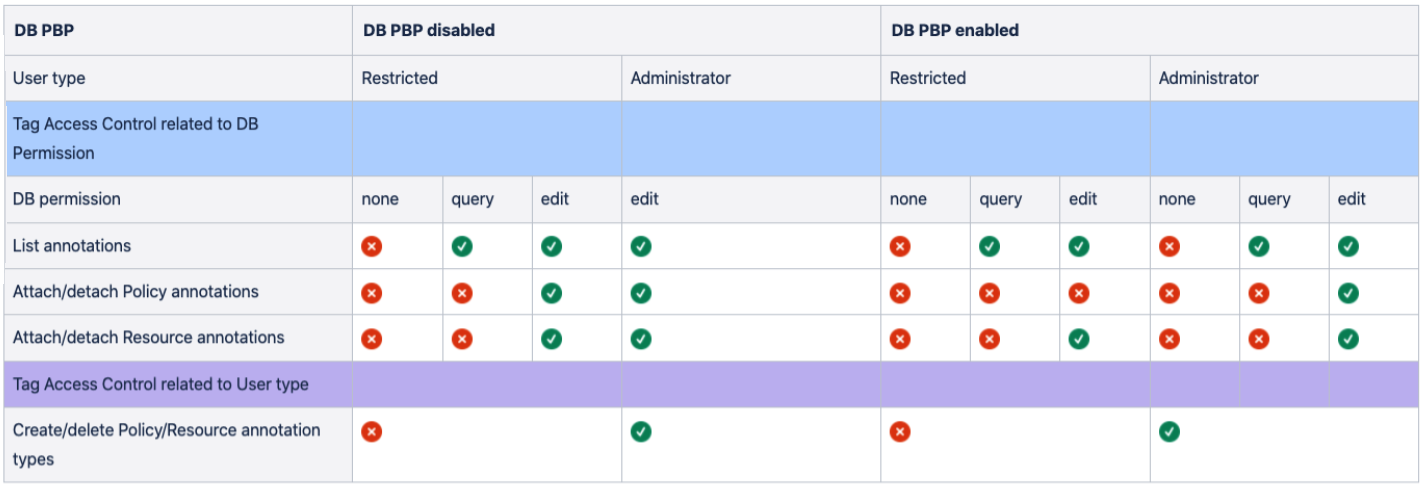
Access Control Matrix (ACM) in terms of Operation Security — its usage and purpose | by Ayyappan Subramanian | Medium